We are the partner to boost yourCyber defense
Our comprehensive end-to-end approach addresses both proactive and reactive cybersecurity measures. From strategic guidance at the executive level to specialized technical expertise on the ground, our services, informed by incident response, equip clients to be prepared for cyber threats during both critical situations and periods of stability.

30K+
Followers
Key Solutions & Services
Discover our main offerings for innovative ideas on how to more effectively mitigate your risks.
Cybersecurity Experts
Cybersecurity Training
Managed Security Service

Featured Resource
CISO Services Datasheet
Securing Processes
Ensuring continuity and resilience against compromises or interruptions
vCISO Services
Compliance assistance, risk management, certification process guidance
Hybrid SOC Services
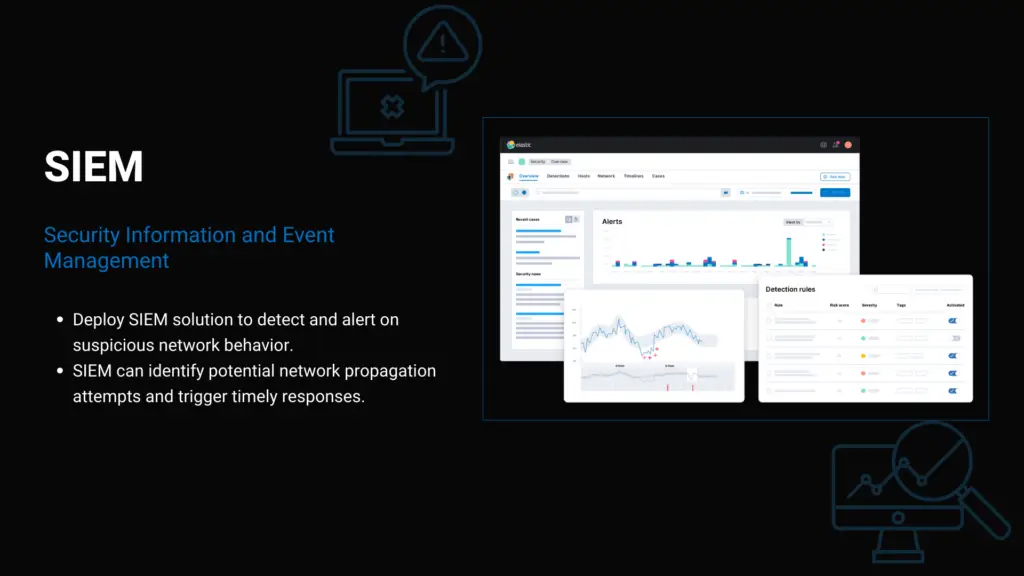
JulieSecurity delivers state-of-the-art SOC services tailored to protect your enterprise against evolving cyber threats. Powered by our Next-Gen SIEM and hybrid SOC platform, we ensure 24/7/365 threat monitoring, detection, and response to safeguard your IT and OT environments.
24/7/365 Monitoring
Around-the-clock expert surveillance to detect and mitigate threats in real-time.
Proactive Threat Protection
Focus on real threats to enhance safety and maintain a secure environment.
Efficient Alert Management
Automated processes prioritize critical threats, ensuring your environment remains safe and secure.
Incident Response Ready
Automated processes prioritize critical threats, ensuring your environment remains safe and secure.

Watch the one-minute video about our supply chain security services
Discover how our supply chain security services can help safeguard your business against cyber threats and disruptions. In just one minute, learn how we assess vulnerabilities, implement robust safeguards, and ensure the resilience of your supply chain. Watch now to see how we can protect your operations and secure your critical assets.







Cybersecurity Wrap-up: SIEM Practices and Tips from NIST
In 2020, proper cybersecurity measures are a vital need for all kinds of organizations. The business world has changed, and now, not only big companies

Organizations Hacked Via BMS: Everyone’s Problem
Building Management Systems (BMS) have been a powerful resource for organizations to achieve superior efficiency. The problem is that, when poorly implemented and maintained, these

Why Protect ICS?
Industrial control systems are a quintessential part of our productive engines. Their development represented a revolution for industrial processes as organizations gained control over every

